What is identity muling, and how can you prevent this new fraud vector?
An identity mule is someone who is compensated for sharing their identity. They may be asked for pictures of their identification documents and video selfies. Or, instructed to create an account and complete an identity verification flow before handing over the account’s credentials to a bad actor.
The fraud cat-and-mouse game is taking a new turn. As organizations get better at detecting deepfakes, some bad actors are using real people’s identities to commit fraud. But it’s not identity theft. In exchange for around $5 to $20, the identity mules share selfies, identification documents, or even create and verify an account for the bad actor.
Fraudsters can’t scale these operations as quickly as they can spin up new deepfakes or synthetic identities. But identity mules are willing accomplices who can legitimately get through selfie checks, making this form of second-party fraud particularly difficult to detect.
Here's what you need to know about this new fraud vector and how you can protect your organization.
What is identity muling?
Identity muling is when a bad actor pays willing accomplices to use their identity.
In some cases, the bad actor pays the mule for pictures and videos of their identification documents and face. The bad actor can later sell the files or inject them into an identity verification process as part of an attack.
But more often, mules are asked to follow the bad actor’s instructions and use their legitimate government ID to complete an identity verification request when creating a new account. Or, in some operations, bad actors give identity mules fake IDs and instruct them to create multiple accounts.
Either way, once the mule creates an account and passes verification, the bad actor takes control of the account and uses it for illicit purposes.
Why fraudsters pay real people to go through identity verification
One reason identity mules are becoming more prevalent is that fraud prevention systems are getting better at detecting other types of attacks.
Fraudsters may try to get past selfie verifications in different ways. One approach is a presentation attack, such as when the fraudster submits a video of a doll, another screen, or a printed headshot. Another is an injection attack, when they use rooted devices, emulators, or virtual cameras to inject videos of deepfakes or real people into the selfie request.
As fraud prevention systems get better at detecting presentation and injection attacks, hiring an identity mule might be the next best option for the fraudster.
However, organized fraud rings won’t take on something as complex as running identity mule operations unless they can get a good “return” on their investment. They might use less sophisticated schemes for lower-value targets and save their mules for higher-value targets.
Identity muling versus identity theft
Some bad actors create digital (and occasionally physical) photobooths to steal victims’ headshots and video selfies. And human trafficking victims who are being held in scam compounds may be forced to use their likeness and documents to complete identity verification requests.
We consider these people victims of identity theft rather than identity mules. Regardless of whether identity mules are aware of what the bad actors are doing, the mules participate willingly. This aligns identity mules with other commonly used fraud terms, such as shipping mules and money mules.
Identity muling | Identity theft |
|---|---|
Someone willingly uses or shares their identity | A bad actor uses a victim’s identity without consent |
Second-party fraud | Third-party fraud |
Passes liveness and injection attack checks | Might fail liveness or injection attack checks |
How is identity muling different from other types of muling?
Muling generally refers to different types of human-assisted fraud, where the fraudster tricks or pays the mule as part of a larger scheme.
Other examples include money mules, people who receive funds into their accounts and then transfer the money. Fraudsters use the mules to launder money, and they often recruit them by posting "work from home" jobs or tricking romance scam victims.
There are also shipping mules, people who receive and forward packages for fraudsters. The fraudster may have bought products using stolen credit cards and shipped them to different addresses to avoid detection. Or, the shipping mule may be unwittingly shipping drugs or other illegal goods.
Although the tactics and goals are different, there are similarities among all these groups:
The mule is typically compensated upfront and might not have any ongoing involvement with the operation.
There may be a fraud ring leader who directs the muling operation and coordinates subsequent fraud attacks.
Muling is also a form of second-party fraud, and it may be illegal even if the mule isn’t knowingly participating in fraud. For example, in the US, money mules can face fines and imprisonment.
In Singapore, scammers, scam recruiters, and members of organized scam groups can now receive a mandatory six lashes from a cane (up to 24, depending on the situation). Scam mules, people who knew or intended for someone else to use their credentials to commit a scam, can receive up to 12 lashes.
What does identity muling look like to fraud fighters?
Identity mule operations range from opportunistic to highly sophisticated.
Basic operations: Fraudsters recruit mules through social media or local networks, pay them directly, and have them complete verifications using their real information. These accounts may reuse the same device, IP address, or physical location.
Advanced fraud rings: Fraudsters scale sophisticated operations by creating fake IDs that have the mule's photo and falsified information. The fraudsters coach mules to take selfies and move mules to different locations to avoid pattern detection. Some operations even spoof IP addresses and take other measures to avoid detection.
If an identity mule ring targets your organization, you might see:
Similar selfies and environments
When the fraud group operates out of a single physical location, you may notice that the selfies new users submit appear oddly similar. You might see very similar backgrounds, such as the same home or office setup. Or, some fraud groups might try to disguise the situation by having mules pose in front of a blank wall or hanging sheet.
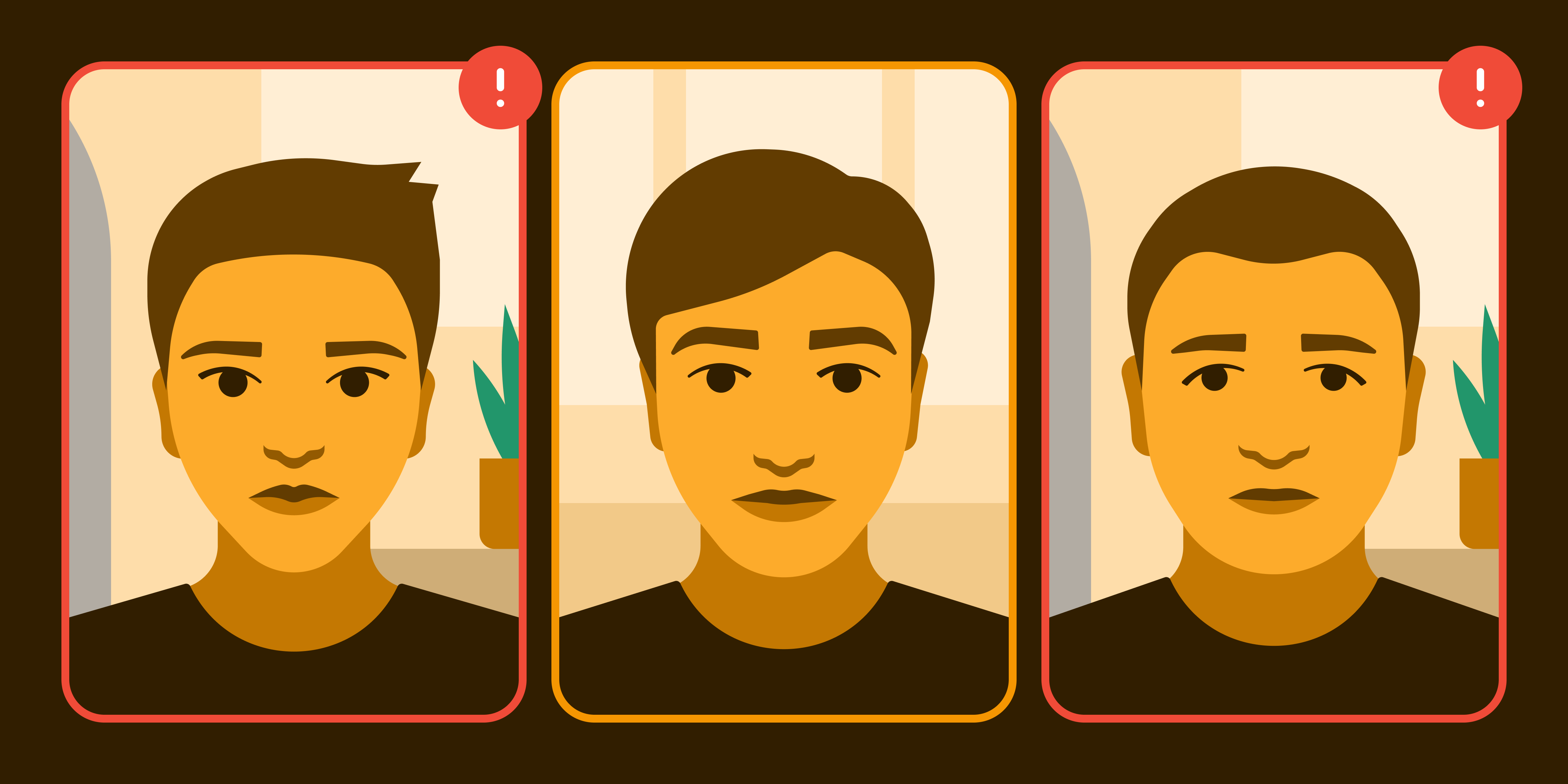
Similar ID images and backgrounds
The government ID submissions may also have a template-like quality to them. If the fraudster is creating fake IDs for the mules, you might notice similarities in the physical document, such as the same date of birth or address. Regardless of the document's authenticity, you may also notice that the IDs are all placed on the same desk or countertop.
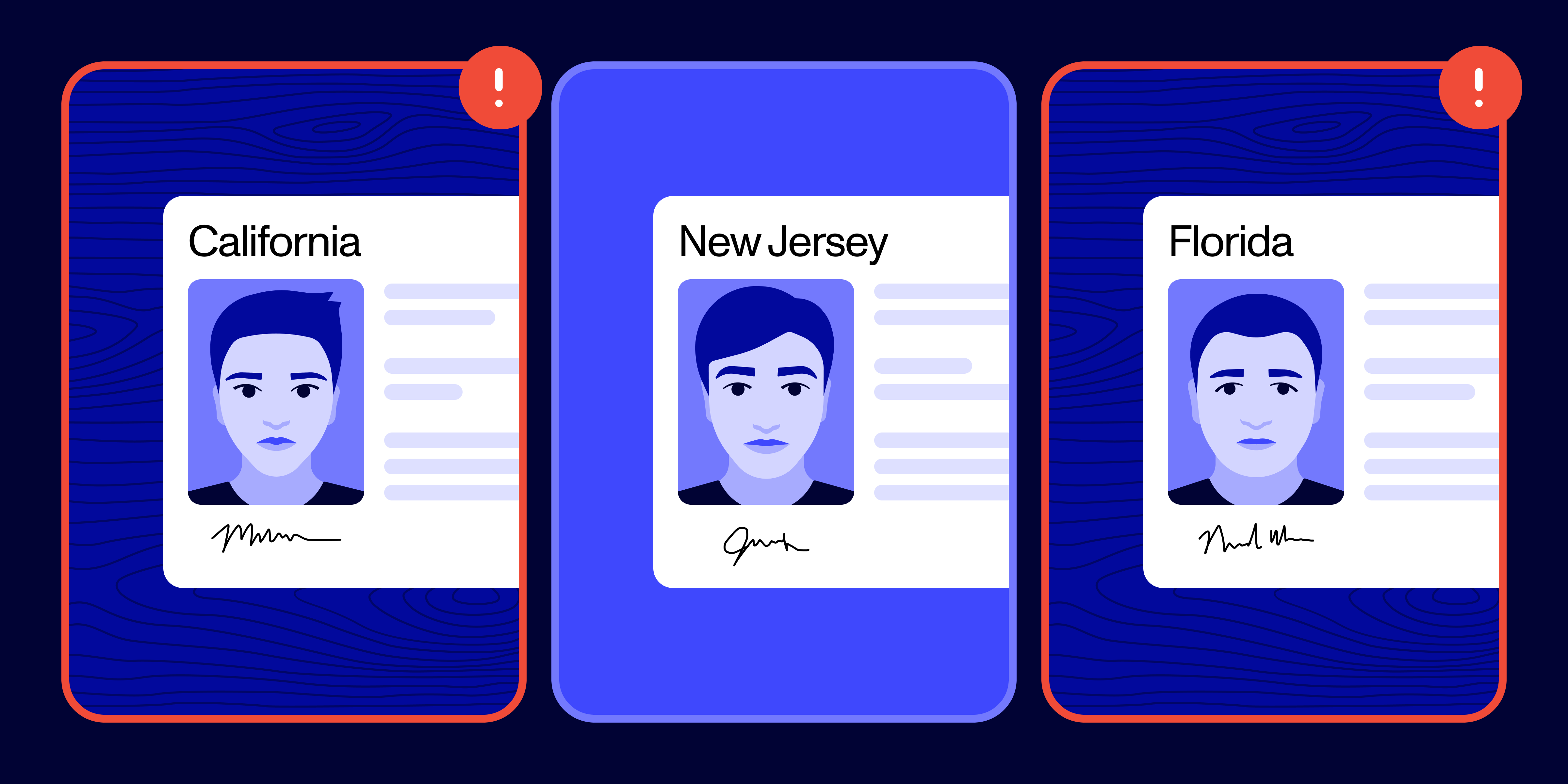
Shared devices or networks
Sometimes, the mules might be instructed to use the same device to create accounts. Even if they’re using their own devices, they might share the same IP address and be located in a region that’s commonly associated with fraud in your environment.
Once the mules create and hand off accounts, the fraudsters might access the accounts using a single device. The process can link the fraudster’s device to multiple accounts. If fraudsters operate from multiple locations, you may notice logins from places that are too far apart for someone to travel between the login attempts.
How to fight identity mule rings and attacks
Identity mules are real people, and they can legitimately pass standard liveness detection during identity verification. As a result, detecting identity mules can sometimes be more difficult than fighting the most sophisticated AI-powered attacks.
But there are a few steps you can take to consistently stay ahead of fraudsters who rely on mules.
Monitor and stack risk signals
You might detect identity mule fraud based on different risk signals and velocity checks. Stack signals to improve recall and precision, and be particularly mindful of the following risk signals:
Shared IP addresses
VPN, Tor, or proxy use
Located in a high-risk area
Impossible travel between logins
Shared browser or device fingerprints
Behavior signals and patterns can also be important. For example, users who attempt to quickly change the account credentials or details during the second login might be riskier. If you also notice some of the risk signals above, that might be a sign that you should flag the account.
Uncover connections with link analysis
Once you confirm an account belongs to an identity mule, you can use link analysis to find connected accounts in your system. Look for shared devices, IP addresses, email addresses, phone numbers, document details, and image similarities.
Link analysis can quickly uncover connections even when there are several degrees of separation. With some link analysis tools, you can use the insights to determine when to require reverification. You also might be able to use the results as real-time signals during identity verification.
For example, you could automatically block accounts that have the same device fingerprint as the previously caught identity mule. Or, you could automatically flag accounts when two or more accounts try to submit nearly identical identification documents.
Run database verifications
A database verification allows you to cross-check information from the user’s identifying documents with issuing or authoritative sources. It’s often part of a multi-layered fraud defense, and it can be effective when fraudsters create fake IDs for the identity mules.
Require selfie reverification before high-risk transactions
Asking users to reverify their accounts before approving high-risk actions can be a good deterrent because fraudsters usually won’t be able to contact the original identity mule.
You likely don’t want to add friction for every user, but you can use dynamic, risk-based flows to only require reverification from users when other risk signals are present.
How Persona can help
Identity mules are emerging as a trending and dangerous fraud vector. Forcing fraudsters to attempt to use identity mules could be considered a win because identity mules are more expensive for fraudsters to scale. But the fight never stops for fraud fighters, and identity mules can also be more difficult to detect than other fraud vectors.
Persona's verified identity platform has the tools and features to detect and automatically stop identity mule operations:
Graph, Persona’s link analysis tool, comes with automatic image similarity detection, which can be a powerful tool against identity mules and deepfake fraud. When you identify one mule, Graph helps you find the entire identity mule ring by uncovering connections. You can also run multi-hop analysis in near real-time and use the results as conditional steps when users visit your site or verify their identity.
Sentinel allows you to continuously capture device, network, and behavioral signals from mobile and browser sessions. Use these signals with Graph to take down identity mules and fraud ring leaders before the users create or log into an account.
Dynamic Flow allows you to automatically adjust verification requirements based on risk signals. Design your Workflows with the no-code editor and then trigger selfie reverification when users attempt high-risk actions, flag or automatically block suspicious users, and give your legitimate users a low-friction experience.
Reports provide additional risk signals from Persona and Marketplace partners, such as SentiLink and Telesign, helping you build a comprehensive risk profile for each user.
Start for free or request a demo to see how Persona helps fraud teams fight identity mules and fraud rings.
FAQs
Is identity muling illegal?
Toggle description visibility
Identity muling may be illegal in many jurisdictions, even if the person isn't knowingly committing or participating in fraudulent activity. Identity mules may also have trouble creating and using legitimate accounts for themselves in the future if their identity is associated with fraud or policy abuse.
Do identity mules know they’re participating in fraud?
Toggle description visibility
Some identity mules might suspect or know that the bad actors will use the verified account to commit fraud. Others may be unaware or deliberately stay ignorant to justify the activity.
What industries are most targeted by identity mule rings?
Toggle description visibility
Fraudsters may use identity mules to target platforms where a verified account can be especially valuable. High-risk industries include financial services, fintechs, crypto, ecommerce, marketplaces, ticketing platforms, and online gaming.
How much do identity mules get paid?
Toggle description visibility
Bad actors might pay identity mules different amounts depending on the location, request, and the fraudster’s motivation. There are reports of people being paid $5 to $20 for pictures of their IDs, selfies, and short videos of their faces.
Why are fraudsters using identity mules instead of deepfakes?
Toggle description visibility
Modern fraud detection tools are getting better at catching deepfakes and other AI-generated content. While identity muling is harder and more expensive to scale, it may also be more effective at getting through identity verification checks. Fraudsters who think they'll get a good ROI with verified accounts may prefer using identity mules over deepfakes.

